Third-Party Risk Management Framework: A Step-by-Step Implementation Guide
Building a robust third-party risk management framework protects your organization from vendor-related threats while maintaining regulatory compliance. Companies increasingly rely on external vendors, making systematic risk management essential for business continuity.
What is a Third-Party Risk Management Framework?
A third-party risk management framework is a structured approach organizations use to identify, assess, monitor, and mitigate risks associated with external vendors, suppliers, and service providers. The framework covers cybersecurity, compliance, financial, operational, and reputational risks throughout the vendor lifecycle.
This systematic approach provides comprehensive visibility into potential risks from initial onboarding to relationship termination. Organizations maintain strong security postures and compliance by implementing standardized processes.
8-Step TPRM Framework Implementation Guide
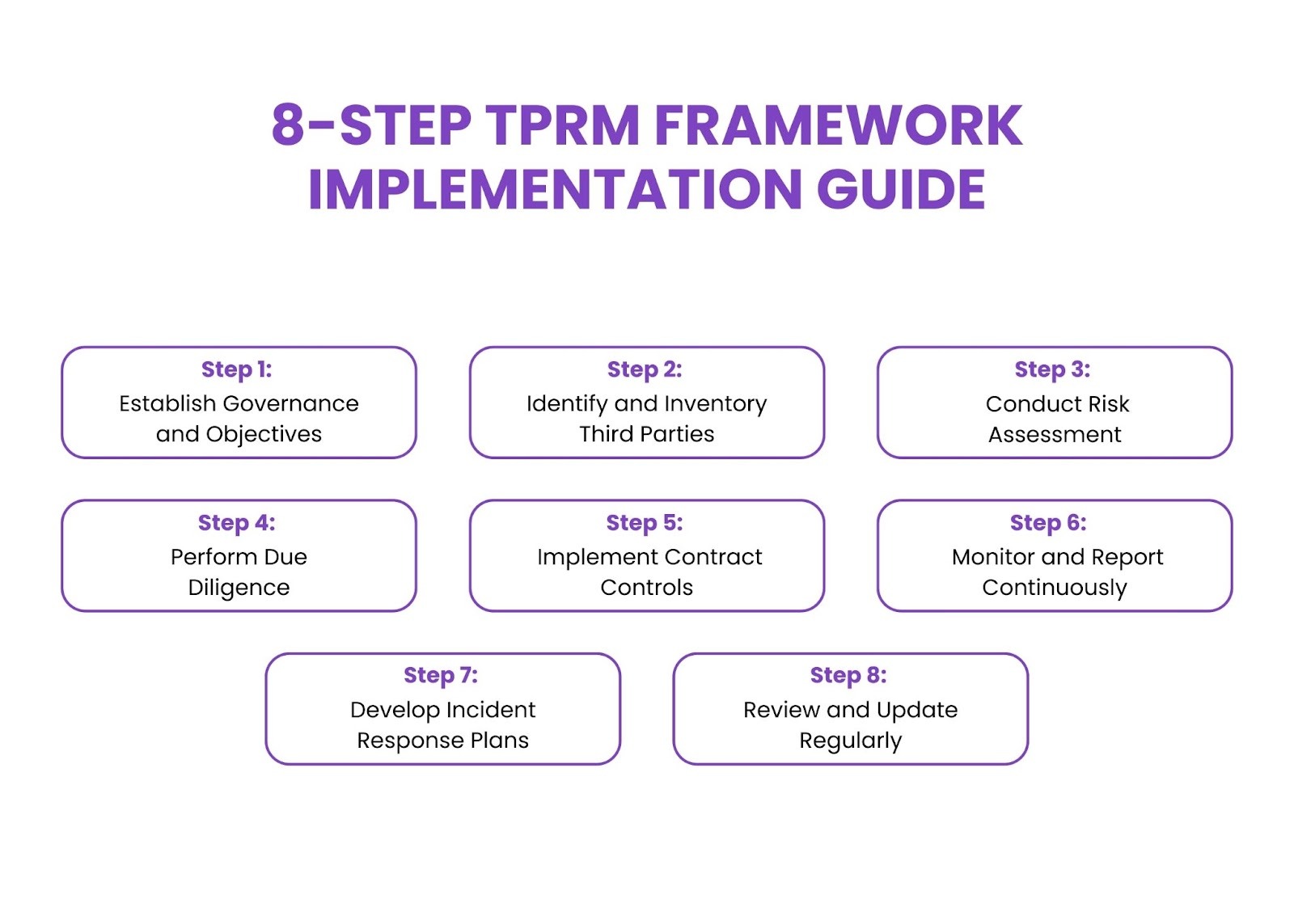
Step 1: Establish Governance and Objectives
Define clear goals, scope, and expected outcomes for your third-party risk management program. Create governance structures with designated ownership and cross-functional collaboration between procurement, IT security, compliance, and legal teams.
Document policies outlining risk tolerance and compliance requirements aligned with organizational strategies.
Step 2: Identify and Inventory Third Parties
Develop a comprehensive catalog of all third-party relationships, including vendors, suppliers, contractors, and service providers. Categorize relationships by risk level, business criticality, and operational impact.
Classify vendors based on data access, service criticality, and potential business impact. High-risk vendors require more intensive monitoring than low-risk relationships.
Step 3: Conduct Risk Assessment
Evaluate potential risks across multiple categories, including cybersecurity measures, financial stability, compliance status, operational capabilities, and business continuity plans. Use standardized assessment methodologies, including questionnaires and security reviews.
Document risk findings and establish risk ratings for prioritization and resource allocation decisions.
Step 4: Perform Due Diligence
Execute thorough evaluations before onboarding new vendors. Verify vendor identity, compliance status, and security certifications. Review financial statements and past performance records.
Validate vendor claims through independent verification and reference checks.
Step 5: Implement Contract Controls
Develop contracts with clear risk management clauses, security requirements, and compliance obligations. Include provisions for audits, incident response, data protection, and performance monitoring.
Specify service level agreements and reporting requirements. Establish liability allocation and termination procedures.
Step 6: Monitor and Report Continuously
Implement ongoing monitoring processes to track vendor performance, compliance status, and risk exposure. Use automated tools for real-time risk detection and incident alerting through vendor risk management platforms.
Create regular reporting mechanisms, including risk dashboards, compliance updates, and incident summaries with escalation procedures for high-risk situations.
Step 7: Develop Incident Response Plans
Create comprehensive incident response procedures for vendor-related security breaches, compliance violations, or service disruptions. Define roles, responsibilities, and communication protocols for incident management.
Establish coordination mechanisms with vendors for joint incident response activities.
Step 8: Review and Update Regularly
Conduct periodic reviews to adapt to evolving risks and organizational needs. Update policies and risk assessments based on emerging threats and best practices.
Solicit stakeholder feedback and perform self-audits to identify improvement opportunities.
NIST Third-Party Risk Management Framework
The NIST Cybersecurity Framework 2.0 provides comprehensive guidance for managing third-party and supply chain risks. NIST 800-53 includes specific supply chain risk management controls, while NIST 800-161 focuses on supply chain risk management throughout vendor relationships.
Third-Party Risk Management Lifecycle
The vendor lifecycle includes onboarding, active management, and termination. Each phase requires specific activities to maintain risk oversight.
Best Practices for TPRM Implementation
Focus resources on the highest-risk vendors based on data access and business impact. Deploy automated tools for assessment, monitoring, and reporting to improve efficiency.
Maintain clear communication with vendors about expectations. Foster collaborative relationships that encourage transparency and proactive risk management.
Common Implementation Challenges
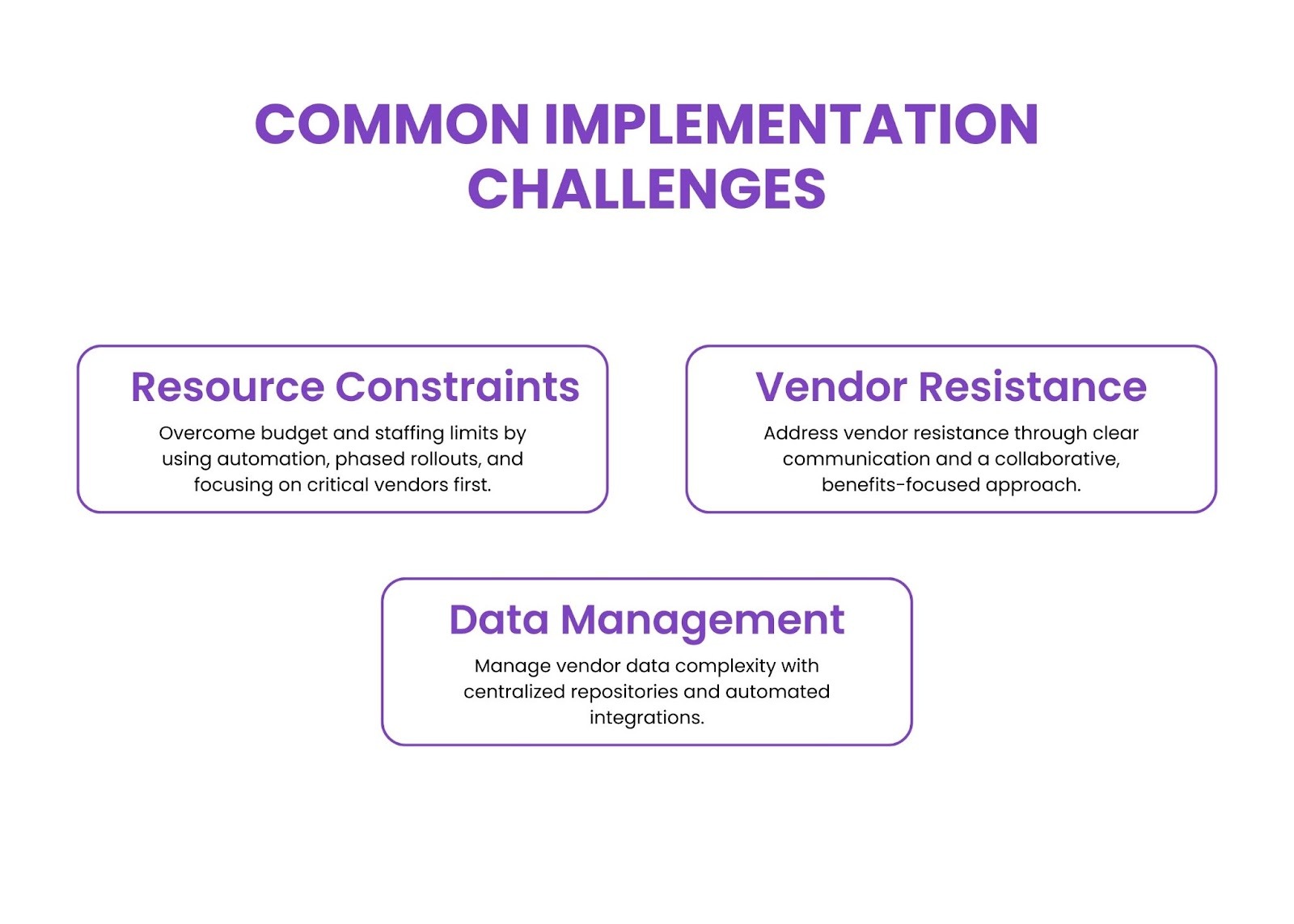
Resource Constraints
Limited budget and staffing often hinder framework implementation. Address challenges through automation, third-party services, and phased approaches, prioritizing critical vendors.
Vendor Resistance
Some vendors resist assessment requirements due to confidentiality concerns. Overcome resistance through clear communication about mutual benefits and collaborative approaches.
Data Management
Managing large volumes of vendor data creates complexity. Implement centralized repositories and automated integration tools for better data quality.
Benefits of TPRM Framework Implementation
Comprehensive frameworks provide clear insights into vendor risks, enabling proactive identification and timely mitigation. Structured approaches help organizations meet regulatory requirements while reducing penalty risks.
Standardized processes improve consistency and reduce assessment times while maintaining risk oversight.
Conclusion
Implementing a comprehensive third-party risk management framework requires careful planning and ongoing attention to evolving risks. Organizations that invest in structured approaches gain better visibility, improved compliance, and stronger operational resilience.
Start with clear governance structures and risk assessment processes. Build monitoring capabilities to manage ongoing risks effectively.
Redacto's vendor risk management platform automates third-party risk assessment and monitoring processes. Our AI-powered solution helps organizations implement comprehensive TPRM frameworks while maintaining compliance with regulatory requirements.
Ready to strengthen your third-party risk management? Contact our team to learn how Redacto can help you build effective frameworks. You can also reach us on WhatsApp for immediate assistance.
Frequently asked questions
Key components include risk identification, due diligence processes, contract management, continuous monitoring, incident response, and regular framework reviews.
A framework provides the overall structure for managing vendor risks. A template offers specific tools and documents that support framework implementation.
Automation streamlines vendor assessment, monitoring, and reporting while improving accuracy. Automated tools provide real-time risk alerts and manage vendor data efficiently.
NIST frameworks provide comprehensive guidance for managing vendor and supply chain risks through specific controls and best practices for assessment and monitoring.
Organizations should conduct comprehensive framework reviews annually or when significant changes occur in business operations or regulatory requirements.
Effectiveness metrics include risk reduction indicators, compliance rates, incident response times, and vendor performance scores to identify improvement opportunities.
Contact Us




%20Redacto%20logo_New.png)
