ISO 27001 Third-Party Risk Management: Certification Requirements
ISO 27001 certification requires organizations to demonstrate structured management of third-party risks. Companies working with vendors and service providers must show how they identify, assess, and monitor external relationships to protect sensitive data and maintain compliance.
Key ISO 27001 Controls for Third-Party Risk
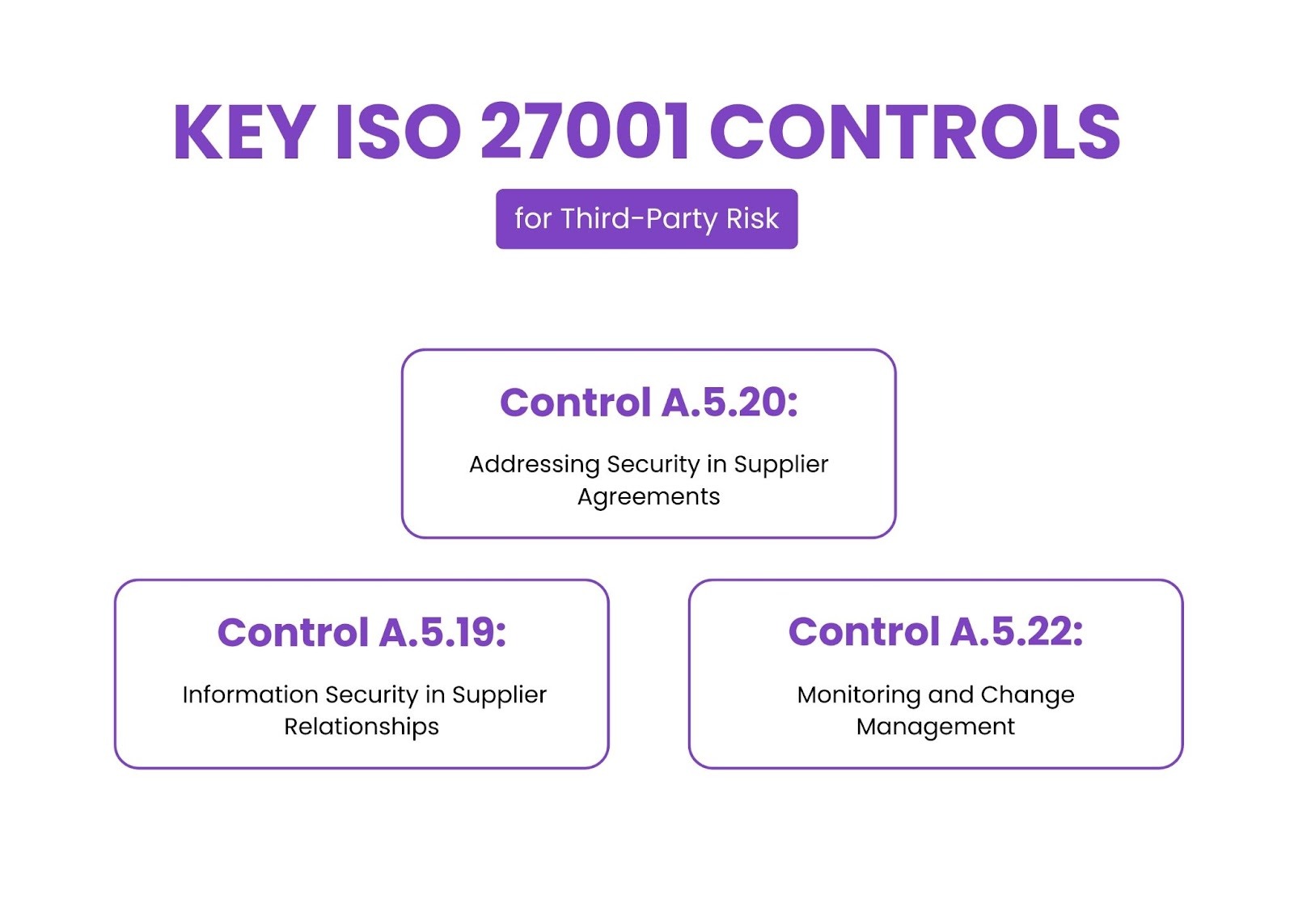
ISO 27001 addresses third-party relationships through specific controls in Annex A that ensure external vendors maintain adequate security standards.
Control A.5.19: Information Security in Supplier Relationships
Organizations must define processes for managing information security risks from suppliers. Companies need to identify which suppliers could affect data confidentiality, integrity, and availability.
Assessment should include reviewing supplier certifications, conducting security questionnaires, and performing due diligence reviews before engagement.
Control A.5.20: Addressing Security in Supplier Agreements
All supplier contracts must include relevant information security requirements. Agreements should clearly define security responsibilities, data handling obligations, and compliance requirements.
Contracts need to specify audit rights, incident reporting procedures, and termination processes when suppliers access sensitive information.
Control A.5.22: Monitoring and Change Management
Regular monitoring helps organizations track supplier security performance through service reviews and audits. Change management becomes critical when suppliers modify services or security procedures.
Core Requirements for Vendor Management
Meeting ISO 27001's vendor risk management requirements involves several key components.
Risk Assessment and Classification
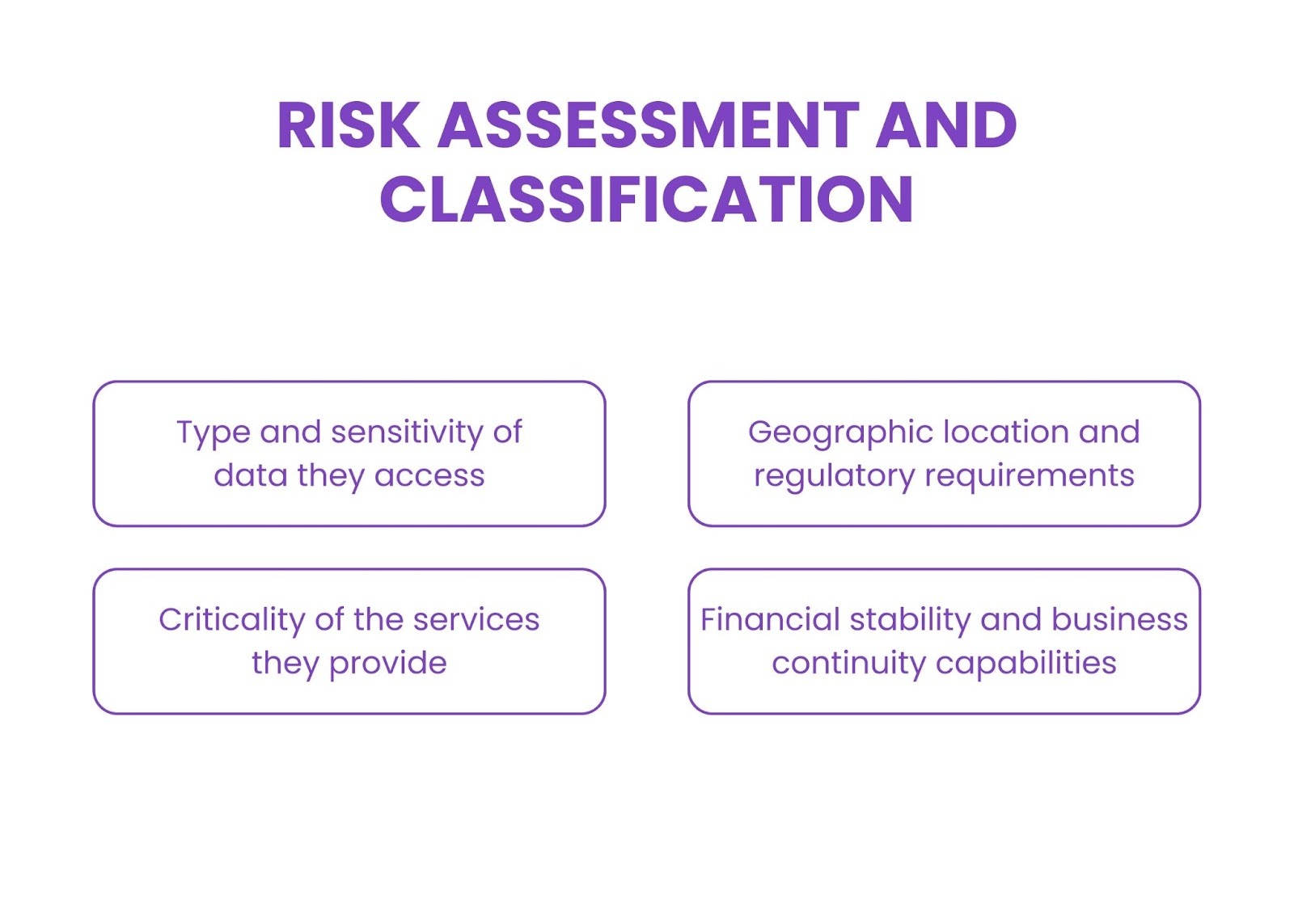
Organizations must conduct risk assessments for all third parties accessing data or systems. Vendors should be classified based on:
- Type and sensitivity of data they access
- Criticality of the services they provide
- Geographic location and regulatory requirements
- Financial stability and business continuity capabilities
Higher-risk vendors require more extensive security assessments and monitoring.
Due Diligence and Security Assessments
Before engaging suppliers, organizations must evaluate security capabilities through certification reviews, questionnaire-based assessments, or on-site security reviews.
Assessments should cover technical security controls, data protection practices, and incident response capabilities.
Contract Security Requirements
Supplier agreements must include comprehensive security clauses addressing data handling, access controls, and incident reporting with clear audit rights and termination procedures.
Implementation Steps for Compliance
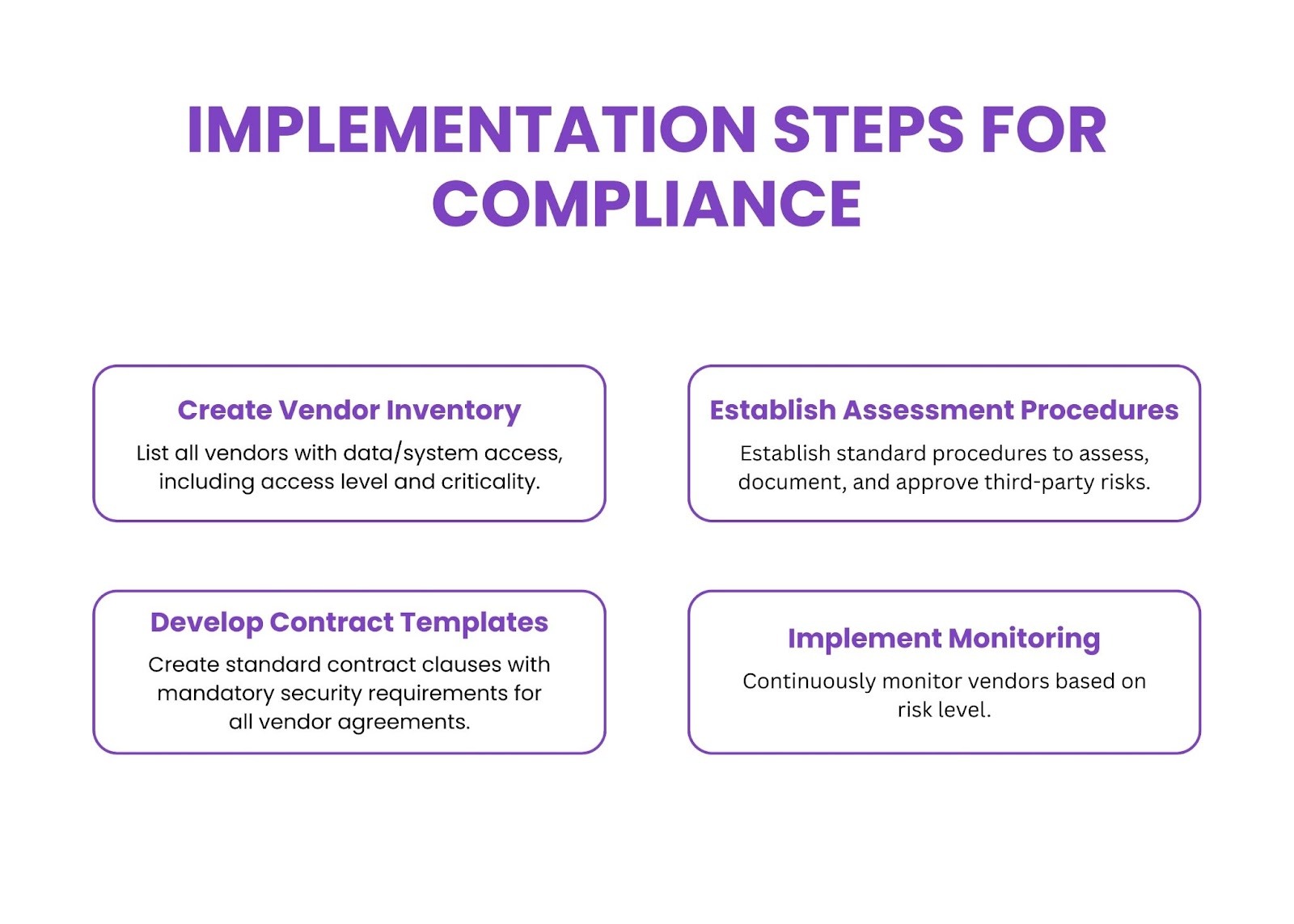
Organizations need a systematic approach to implementing third-party risk management requirements.
Create Vendor Inventory
Develop a comprehensive inventory of vendors and service providers accessing data or systems, including data access levels and service criticality.
Establish Assessment Procedures
Define standardized procedures with assessment criteria, documentation requirements, and approval processes for evaluating third-party risks.
Develop Contract Templates
Create standard contract language, including required security provisions to ensure consistency across vendor agreements.
Implement Monitoring
Establish ongoing monitoring through periodic re-assessments, continuous monitoring tools, or regular security reviews based on vendor risk levels.
Common Implementation Challenges
Organizations face specific challenges when implementing ISO 27001's third-party risk requirements.
Vendor Resistance
Some suppliers resist providing security information or implementing controls. Clear communication about requirements early in procurement helps set expectations.
Multiple Compliance Frameworks
Vendors serving multiple clients need organizations to balance specific ISO 27001 needs without creating excessive burden.
Maintaining Current Information
Vendor security postures change over time. Organizations need processes using automated monitoring tools and regular communication to track changes.
Audit Preparation Practices
ISO 27001 auditors examine third-party risk management practices. Proper documentation is essential for demonstrating compliance.
Auditors review vendor risk assessments, contract security provisions, and monitoring reports. Organizations should maintain organized documentation showing systematic vendor management approaches.
Document how you learn from vendor incidents to improve risk management processes, demonstrating continuous improvement.
Technology Solutions To Meet ISO 27001 Requirements
Organizations leverage technology platforms to manage vendor relationships efficiently and meet ISO 27001 requirements.
Vendor risk management platforms automate risk assessments, track compliance status, and generate audit reports, reducing administrative burden significantly.
Conclusion
ISO 27001's third-party risk management requirements help organizations maintain security while working with external partners. Success requires systematic vendor assessment, contract management, and ongoing monitoring.
Organizations implementing comprehensive programs often exceed certification requirements while reducing security risks and improving vendor relationships.
Ready to strengthen your program? Contact our experts to learn how Redacto helps meet ISO 27001 requirements. Connect on WhatsApp for immediate assistance.
Frequently asked questions
The primary controls are A.5.19 (supplier relationships), A.5.20 (supplier agreements), and A.5.22 (monitoring and change management).
Assessments should be reviewed regularly and whenever significant changes occur in vendor services or business relationships.
While certifications provide value, ISO 27001 requires organizations to assess specific risks related to their business relationships.
No, ISO 27001 supports risk-based approaches where assessments should be proportionate to vendor risk levels.
Auditors review vendor inventories, risk assessments, contract provisions, monitoring reports, and evidence of regular reviews.
Organizations should work with vendors on remediation plans, implement additional controls, or terminate contracts if risks cannot be managed.
Contact Us




%20Redacto%20logo_New.png)
