What Is Inherent Risk? Definition, Key Factors, and Examples for Smarter Risk Management
Frequently asked questions
Inherent risk exists before any controls are applied, while control risk is the chance that existing controls will fail to prevent or detect problems.
Assessments should be reviewed annually at a minimum, with updates triggered by significant business changes, new regulations, or major implementations.
Inherent risk assessment identifies which business processes are most critical to protect, informing priorities for business continuity and disaster recovery planning.
No, inherent risk cannot be eliminated because it stems from the fundamental nature of business activities, but it can be reduced through well-designed controls.
Financial services, healthcare, energy, and heavily regulated industries typically face higher inherent risk due to complex operations and stringent compliance requirements.
Risk exists in every business process, even before you put controls in place. Whether you're handling financial transactions, managing vendor relationships, or overseeing compliance programs, exposure is built into your operations. This baseline level is called inherent risk.
Understanding inherent risk helps you make better decisions about risk management efforts and resource allocation.
What Is Inherent Risk?
Inherent risk is the natural level of risk in any business process before controls are applied. Think of it as raw exposure from conducting business.
This risk stems from:
- Process complexity and transaction volume
- Dependencies on external parties or systems
- Sensitivity of data or assets handled
- Regulatory requirements
A payment processing system handling thousands of daily transactions carries inherent risk due to volume and sensitive financial data. This exists regardless of fraud detection, encryption, or security measures.
Key Factors That Influence Inherent Risk
Several factors can increase inherent risk levels in your organization:
Process Complexity and Volume
Complex processes with multiple steps, departmental handoffs, or system integration create higher inherent risk. High-volume activities carry more exposure.
Manual Processes and Human Dependencies
Activities relying on manual data entry, spreadsheet workflows, or significant human judgment are more susceptible to errors. Organizations handling sensitive data through manual processes face elevated inherent risk, particularly when data discovery and classification aren't automated.
External Dependencies
Dependencies on third-party vendors, cloud services, or external systems introduce inherent risk beyond your direct control. This is where vendor risk management becomes crucial for monitoring vulnerabilities.
Regulatory Environment
Industries subject to complex or changing regulations face elevated inherent risk. Healthcare, financial services, and other heavily regulated sectors must navigate compliance requirements that shift over time. Organizations benefit from automated privacy impact assessments to evaluate compliance risks.
Inherent Risk vs. Residual Risk
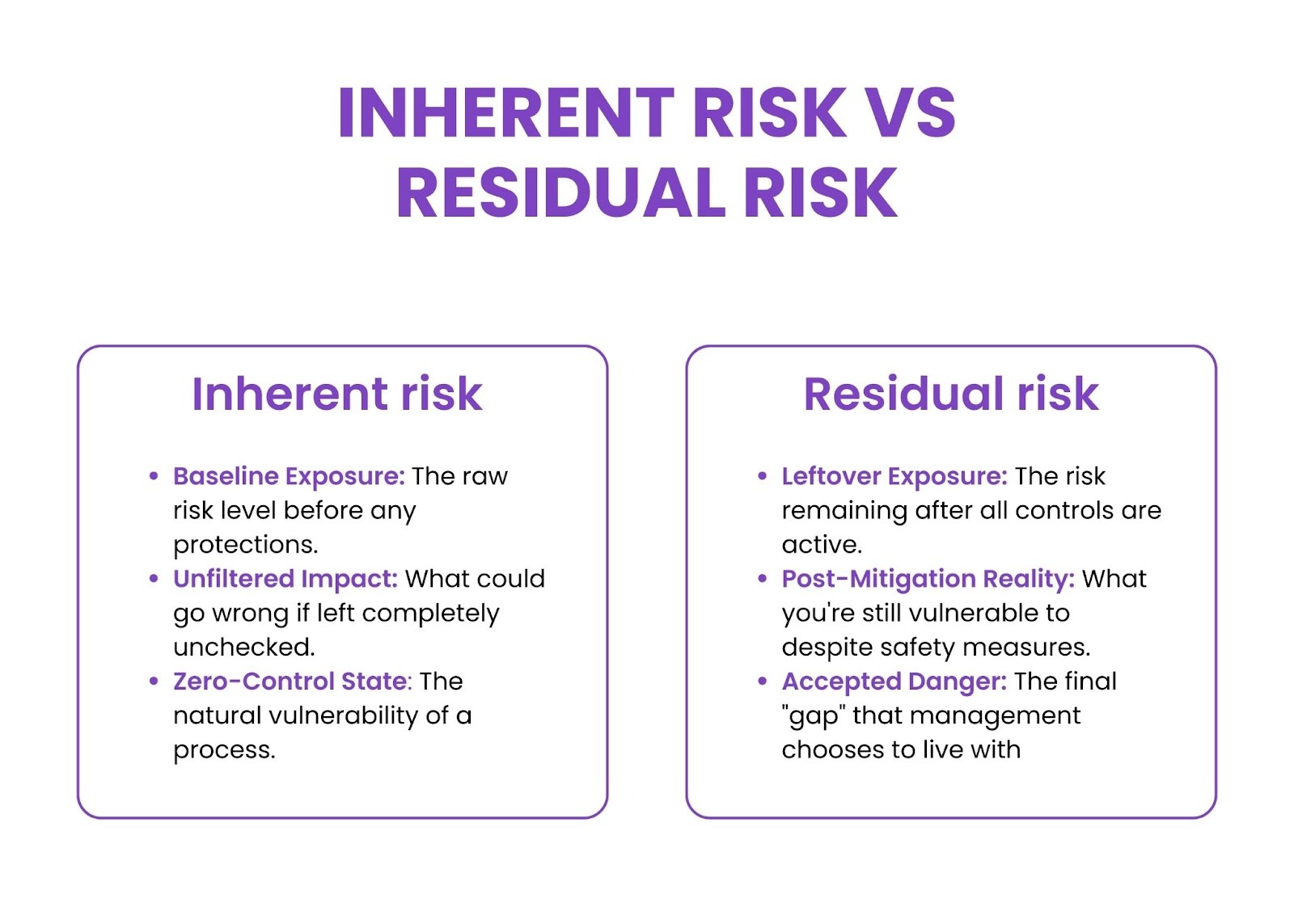
These two concepts work together for a complete risk assessment:
Inherent risk represents baseline exposure before any controls are considered. It shows what could go wrong without protective measures.
Residual risk is what remains after implementing and evaluating controls. It shows remaining exposure despite mitigation efforts.
When evaluating vendor risk management, inherent risk might be high due to sensitive data access. Redacto's VendorShield provides AI-driven risk scoring and continuous monitoring to assess third-party risks effectively.
How to Assess Inherent Risk
Effective assessment follows these steps:
Identify Risk Scenarios
Map potential problems without considering existing controls. Consider activities, decision points, external factors, and dependencies.
Evaluate Likelihood and Impact
For each scenario:
- Likelihood: How often might this risk occur without controls?
- Impact: What would be the consequences?
Calculate Risk Score
Use: Inherent Risk = Likelihood × Impact
Rate both on scales (1-5 or Low/Medium/High) to prioritize resources.
Real-World Examples
Financial Services
A community bank processing loan applications manually faces inherent risk from sensitive data handling, departmental handoffs, and regulatory requirements.
Healthcare
Hospitals managing patient scheduling through legacy systems encounter inherent risk from patient safety implications and HIPAA compliance requirements.
Technology Companies
SaaS providers relying on cloud infrastructure face inherent risk from external dependencies and multi-vendor complexity.
Best Practices for Managing Inherent Risk
Conduct Regular Assessments
Schedule reviews when launching products, entering markets, implementing technologies, or facing regulatory changes.
Engage Cross-Functional Teams
Include operations, IT, security, compliance, and finance for comprehensive risk identification.
Link Assessment to Control Design
Your data protection and privacy controls should be proportionate to inherent risk levels.
Common Assessment Mistakes

Confusing Controls with Risk Factors
Avoid considering existing controls when assessing inherent risk. Inherent risk exists before controls are applied.
Relying Only on Historical Performance
Past performance doesn't indicate inherent risk levels. Processes might carry significant risk but have been protected by controls.
Using Generic Categories
Focus on specific scenarios rather than broad categories. Specificity enables decision-making.
Treating Assessment as a One-Time Activity
Inherent risk profiles change due to technologies, regulations, and market conditions. Regular reassessment maintains relevance.
Conclusion
Inherent risk represents the foundation of effective risk management. Understanding natural exposures before considering controls enables informed decisions about resource allocation and priorities.
Redacto's AI-powered platform helps organizations identify, assess, and manage inherent risks across operations. Our Privacy Engine automates data discovery, while VendorShield offers risk scoring for third-party dependencies. With DPDP, GDPR, and CCPA compliance support, Redacto transforms privacy compliance into trust.
Contact our team to learn how Redacto builds resilient risk management programs, or connect via WhatsApp to discuss your needs.
Contact Us




%20Redacto%20logo_New.png)



.jpg)